External Attack Surface Management (EASM) Platform
External Attack Surface Management (EASM) Platform
#1 Asset Coverage with Laser-Focused, Actionable Intelligence
Gain complete visibility over your external attack surface. Understand your most critical vulnerabilities. Manage risk remediation seamlessly.



Manage Your Attack Surface with Confidence
-
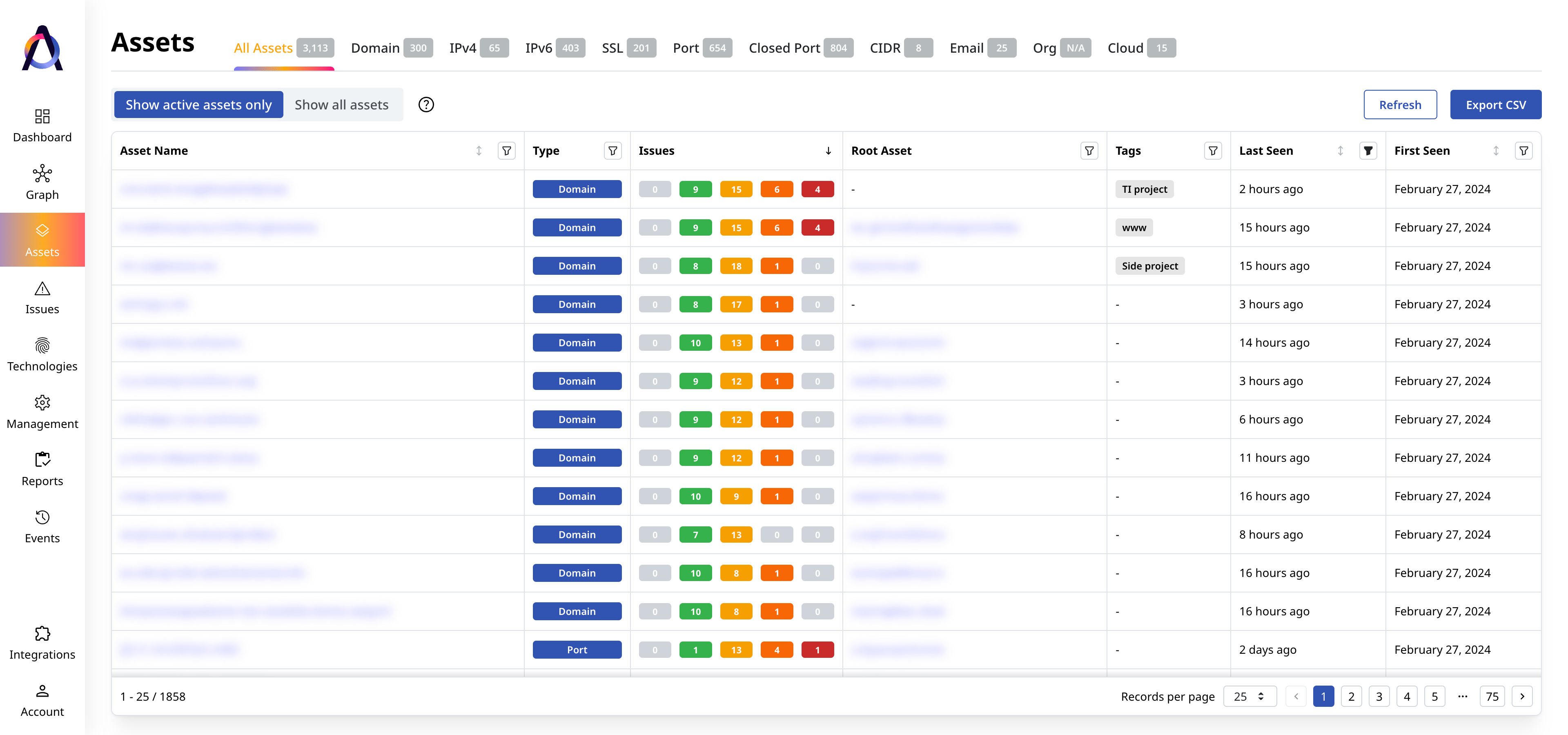
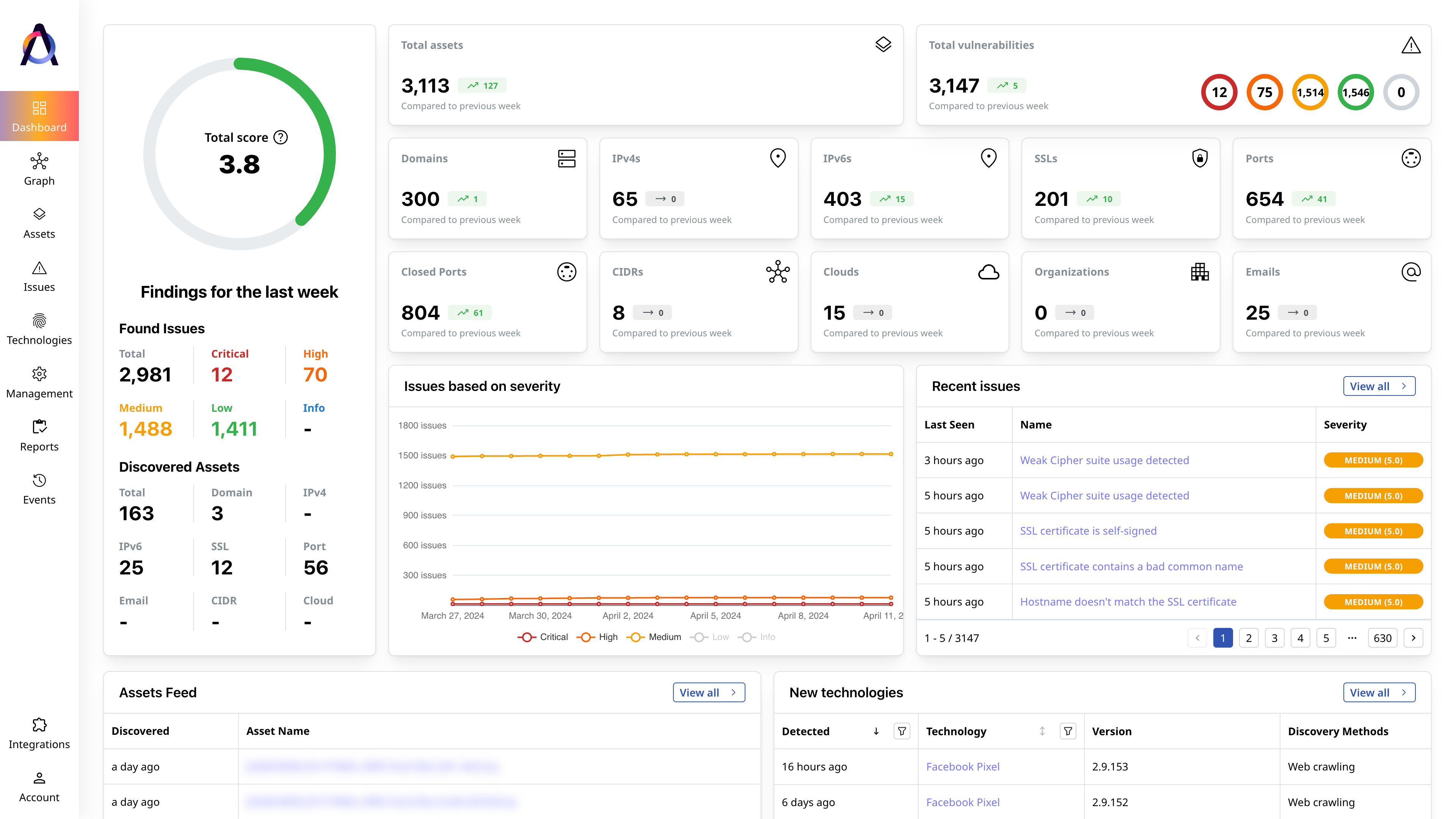
Identify critical security gaps
Prioritize security issues based on their severity, exploitability, and potential impact.
Learn More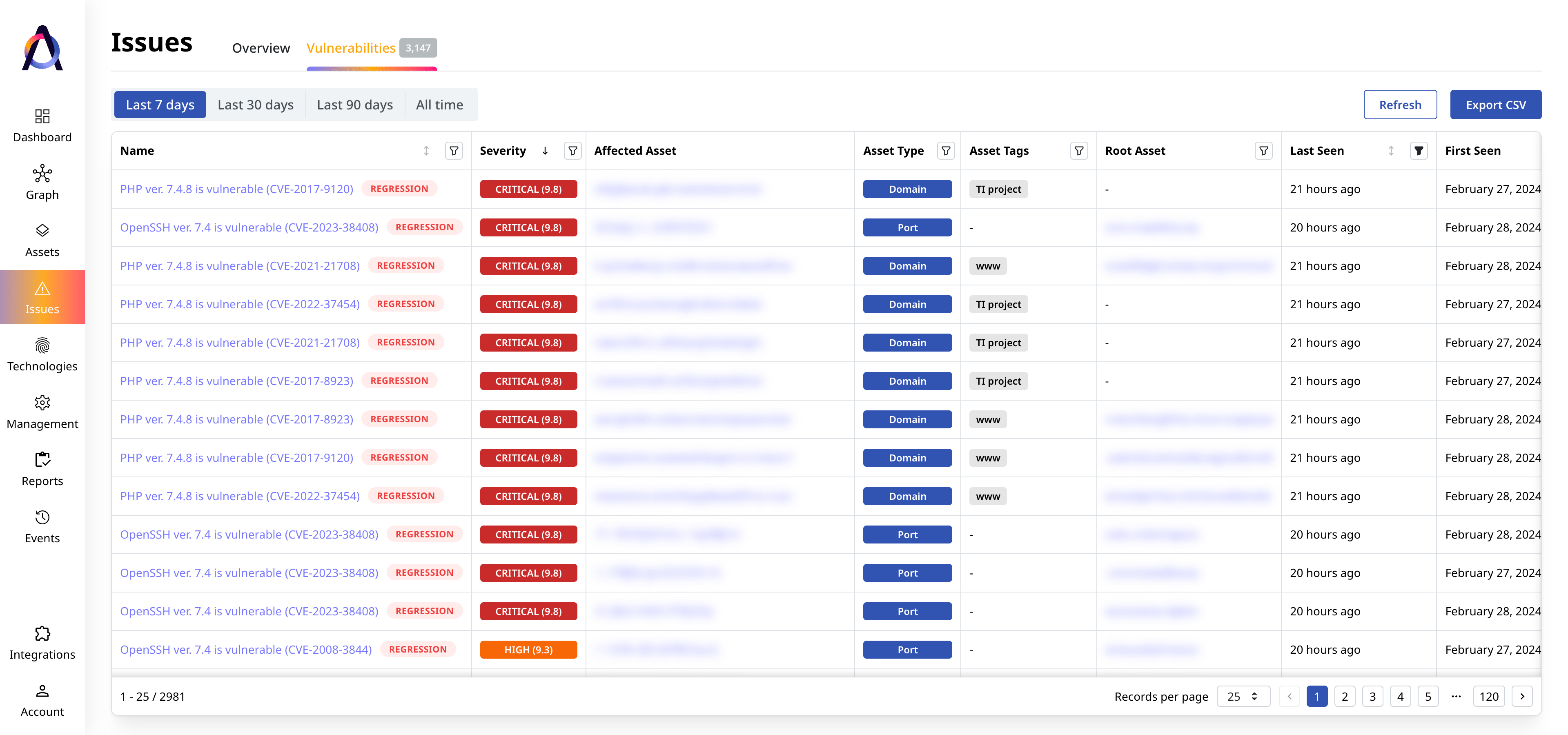
-
Plan and automate remediation
Analyze security weaknesses, automate the allocation of remediation tasks, and monitor progress.
Learn more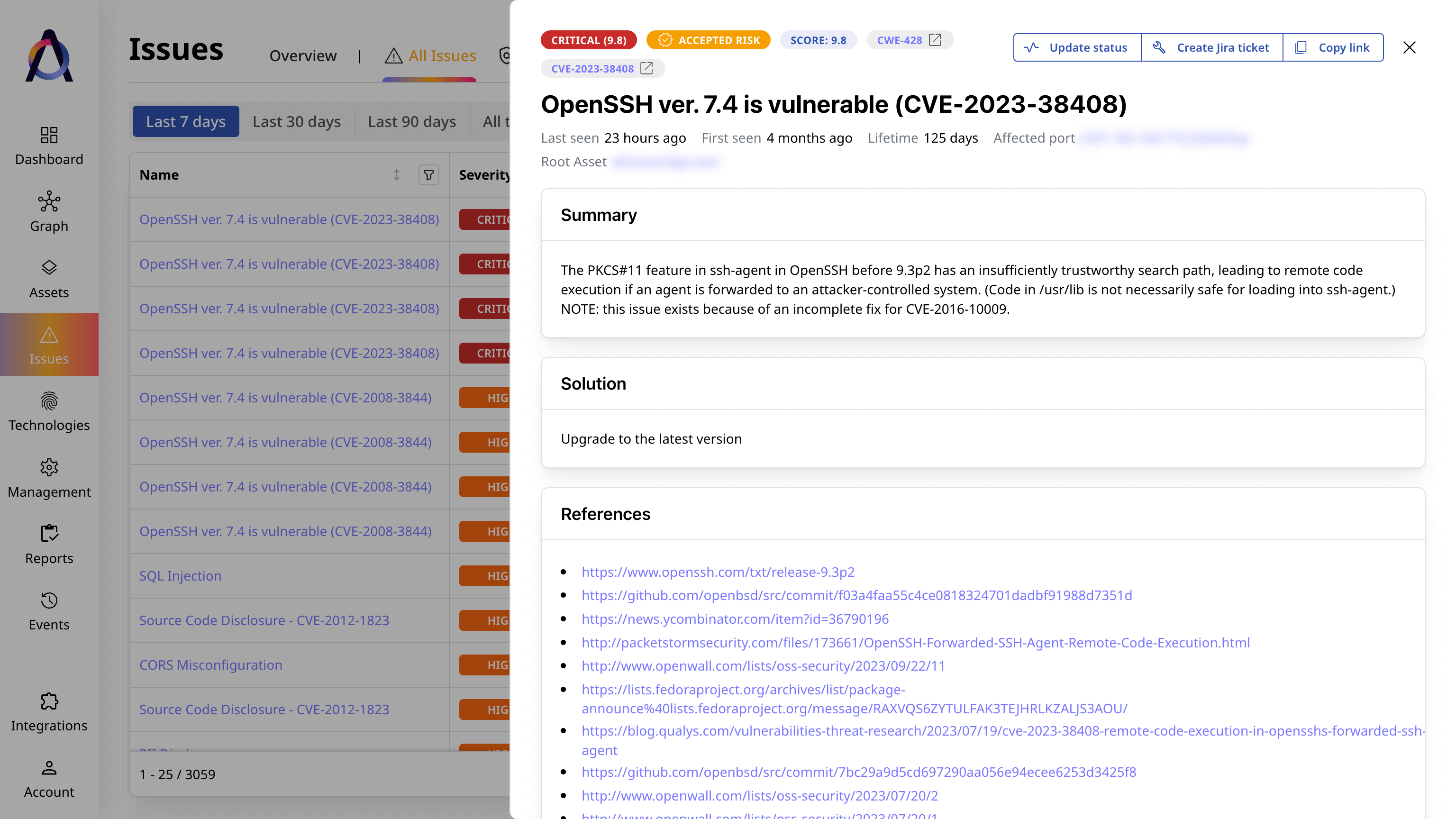
-
Continuously monitor your attack surface
Track new assets and issues as your digital perimeter and the threat landscape evolve.
Learn more
97%
more total assets found3x
as many unique assets found10+
asset types trackedSolutions per Use Case and Industry
-
Learn more
Reduce Your External Attack Surface
Continually eliminate pressing attack vectors in your expanding digital perimeter.
-
Learn more
Enhance Shadow IT Visibility
Discover unsanctioned, forgotten, and misconfigured assets before attackers can exploit them.
-
Learn more
Manage Your Threat Exposure
Proactively identify exposed assets and address the critical issues affecting your security posture.
-
Learn more
Assess Mergers and Acquisitions Risks
Obtain insights into target candidates’ security posture and inherited cyber risks.
-
Learn more
Financial Services
Safeguard financial data from breaches and other threats.
-
Learn more
Online Retail
Secure customer data and business operations.
-
Learn more
IT and SaaS
Keep hosted applications and connected IT infrastructures safe.
-
Learn more
Government
Guard the nation and critical infrastructures against persistent threats.
-
Learn more
Healthcare
Protect patient data and connected medical systems.
-
Learn more
Entertainment
Avoid business interruption, IP theft, and PII leaks.
What security experts say
Featured Resources

Scaling Up? 4 Critical Questions to Manage Your Expanding Attack Surface
Standing still is not an option for organizations that want to succeed. Companies must constantly strive for growth by expanding into new markets, lau[...]

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

Your Digital Supply Chain Is Expanding Your Attack Surface
As organizations increasingly rely on third-party vendors and suppliers for their day-to-day operations, their digital ecosystem also grows more compl[...]